🛡️AWS Cloud Security Deep-Dive
VaultIQ Global Solutions Ltd enables organisations to build secure AWS environments with identity control, encryption, network segmentation, proactive threat detection, and compliance automation — all delivered with Infrastructure-as-Code and audit-ready evidence.
Designed for public-sector & regulated workloads
Fast deployment using reusable Terraform & IaC patterns
Proven governance at enterprise scale
📞 Book a Discovery Call → Free 60–90 mins
What We Deliver
Mapped to CIS, NCSC, ISO 27001 & SOC 2
• Least-privilege identity & access
• Encryption at rest & in transit
• Multi-AZ network security & WAF protection
• GuardDuty + Security Hub + CloudTrail monitoring
• Evidence packs + runbooks for audits
• Continuous-compliance dashboards
Engagement Options
Essentials — 2–3 weeks
• Baseline hardening for 1–2 environments
• Logging + Security Hub enablement
• IaC delivery + training
Scale — 4–6 weeks
• Multi-account landing zone + SSO
• VPC patterns + WAF/Shield
• Automated detection & response
Enterprise — 6–8+ weeks
• Zero-trust segmentation & ABAC
• DR architecture & compliance mapping
• Organisation-wide SCP governance
Every engagement delivers:
Terraform or CloudFormation IaC
Audit-ready evidence pack
Security runbooks & handover
📌 Controls Implemented — at a Glance
Real-World Case Study — Financial Services
🚀 Scaled from 3 → 15 AWS accounts securely
🛡️ Zero high-severity vulnerabilities at go-live
📉 70% fewer manual compliance tasks
🔁 Terraform-driven automation for repeatability
Tech Used: GuardDuty • Security Hub • IAM Identity Center • KMS • Config • Control Tower
Example Deliverable — AWS Threat Monitoring Dashboard
• Real-time visibility of high-severity threats
• Malicious IP geo-correlation
• Early detection automation
• Compliance deviation tracking


Secure-by-design. Automated-by-default. Audit-ready from day one.
AWS Threat Intelligence & Monitoring Dashboard
This dashboard, developed by VaultIQ Global Solutions Ltd, provides a real-time view of AWS security events through Amazon GuardDuty. It highlights high-severity threats, attack origins, and resource vulnerabilities across global regions. By integrating GuardDuty, CloudWatch, and Security Hub, our team enables clients to detect anomalies early, automate remediation, and maintain compliance with CIS, NCSC, and ISO 27001 standards.
Key Features:
🌍 Global threat map tracking suspicious IPs and regions
📊 Real-time severity and incident analytics across AWS accounts
⚙️ Automated alerting and correlation with CloudTrail and Config
🧠 AI-assisted anomaly detection and event prioritization
🛡️ Integrated with Security Hub for unified compliance monitoring
Purpose in Deep-Dive Section:
This visual exemplifies how VaultIQ’s Cloud Security Engineering practice transforms monitoring into proactive defence. It forms part of our AWS Secure-by-Design Framework, where observability, automation, and audit-readiness converge.
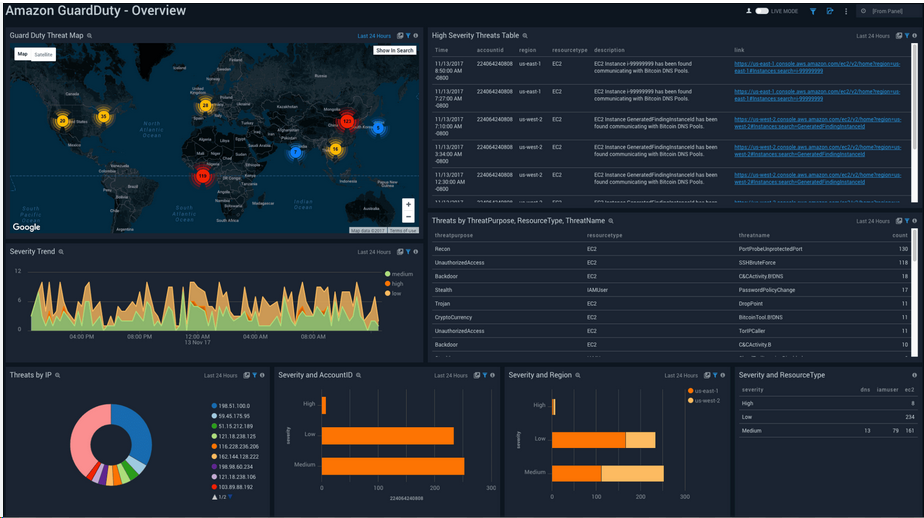
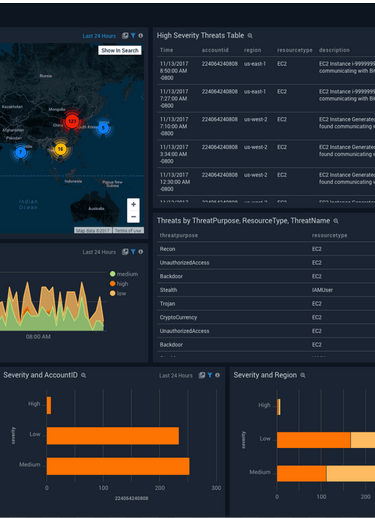
CAWS GuardDuty Dashboard — Real-time global threat visibility powered by VaultIQ
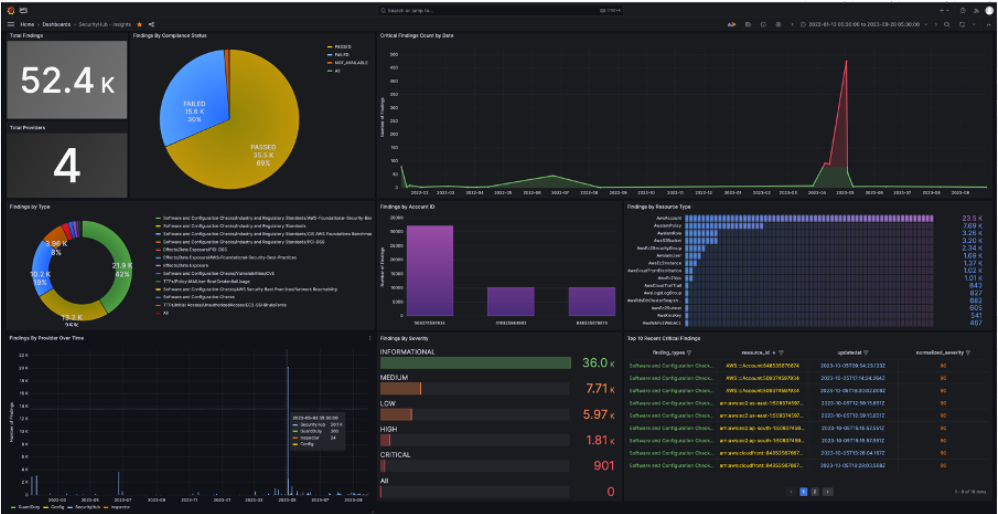
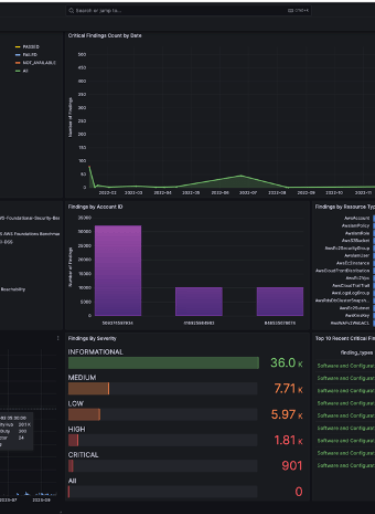
AWS Security Dashboard
This AWS Security Operations Dashboard visualizes live threat detections, compliance metrics, and GuardDuty findings. It showcases VaultIQ’s capability to automate incident detection, streamline investigations, and ensure 24/7 protection across enterprise workloads.
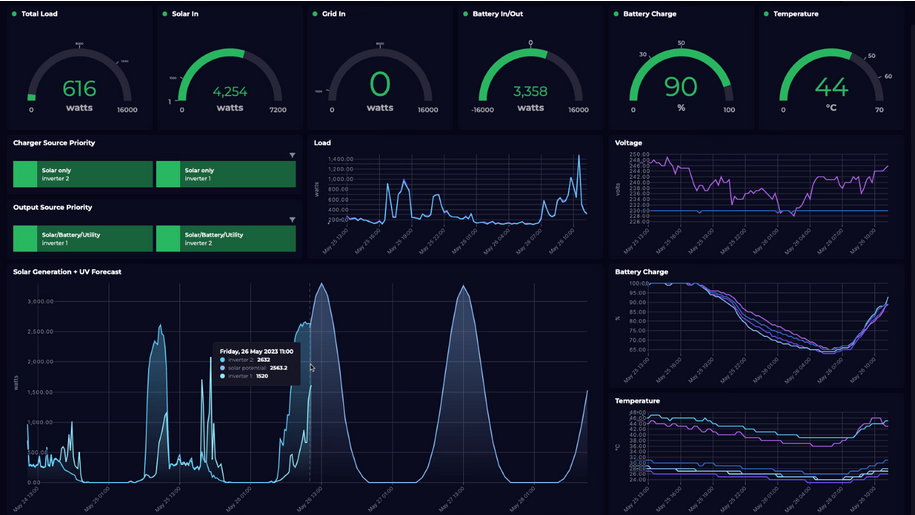
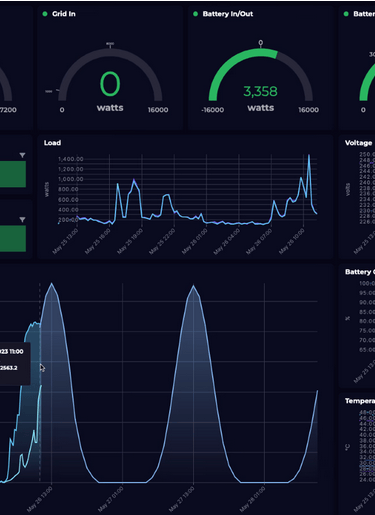
Infrastructure Monitoring Dashboard
The AWS CloudWatch and Grafana dashboard provides deep insights into system health, latency, and performance. VaultIQ engineers use it to monitor cloud workloads, optimize resources, and maintain operational excellence in multi-account environments..
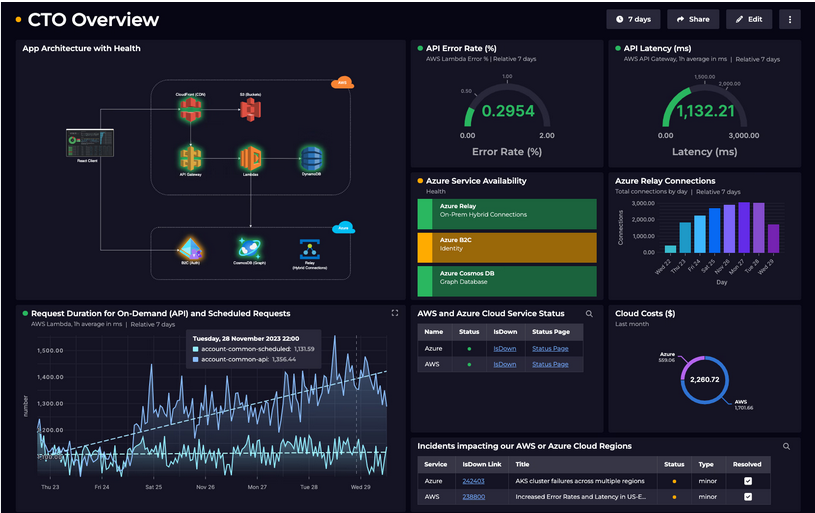
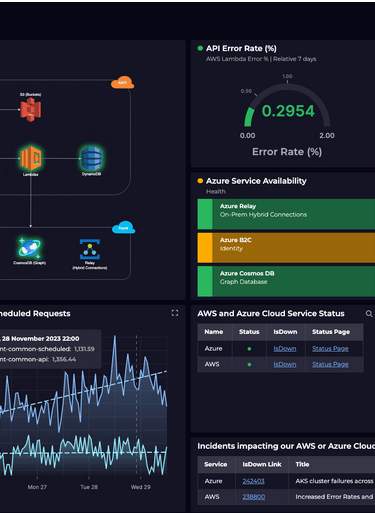
Cloud CTO Overview
The CTO Overview dashboard integrates key DevOps and Security KPIs, offering unified visibility across AWS and Azure systems. It reflects VaultIQ’s expertise in creating observability frameworks that bridge operations, performance, and cybersecurity.


Frequently Asked Questions
Will this disrupt existing workloads?
No — guardrails are introduced gradually & validated first in non-production.
Do we have to use Terraform?
Both Terraform and CloudFormation are supported.
Can this security model extend to Azure or GCP?
Yes — identity, logging, encryption & monitoring patterns are portable.
Tools & Platforms
AWS Organisations • IAM Identity Center • GuardDuty • Security Hub • KMS • CloudTrail
Config • VPC • WAF • Shield • Lambda • Terraform • CloudFormation
Ready to secure AWS?
We’ll design a scalable, compliant cloud foundation for your business.
🔘 Book Free Consultation
🔘 Talk to an AWS Cloud Security Engineer


Partner programme membership statements reflect current registration status. Vendor logos and tier designations are used only where contractually permitted.
© 2025 VaultIQ Global Solutions Ltd
Registered Office: 71–75 Shelton Street, Covent Garden, London, WC2H 9JQ
Registered in England & Wales — Company No: 16662673
Privacy Policy | Terms of Use
